PROGRAM
4th
WSEAS International Conference on
INFORMATION SECURITY, COMMUNICATIONS
and COMPUTERS (ISCOCO 2005)
Puerto De La Cruz,
Tenerife,
Canary Islands,
Spain
December 16-18, 2005
Friday, December 16, 2005
ROOM A’:
Plenary Lecture I
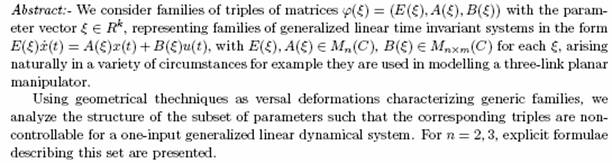
Uncontrollability set for one -
input generalized
dynamical systems depending on parameters
Professor M. ISABEL GARCIA-PLANAS
Departament de Matematica Aplicada I
Universitat Politµecnica de Catalunya,
C. Minera 1, Esc C, 1o-3a
08038 Barcelona, Spain

ROOM A’:
Plenary Lecture II
Statistical Learning for Dependence Mining and
Problem Solving: Fundamentals, Challenges, and a Unified Theory
Professor LEI
XU, IEEE Fellow, IAPR Fellow,
Chair Professor of
Chinese University of Hong Kong
Hong Kong
Abstract: An intelligent system is featured by its abilities of discovering knowledge and skills of problem solvinge, both of which are learned from data. Due to observation noise and a finite size of samples, the learning task faces two challenges. One is finding mathematical representations to suit dependence structures underlying the world. The other is getting a theory to guide learning such that only those reliable dependence structures are learned into mathematical representations with an appropriate complexity that matches the size of samples. This talk consists of two parts. The first provides a summary of existing major mathematical representations for dependence structures and typical learning theories, as well as applications, from a unified perspective under the name of Bayesian Ying Yang learning. The second part briefly introduces the main results by the speaker for solving several typical problems in statistical learning and pattern recognition.
ROOM C’:
Plenary Lecture III
A General Concept for the Modelling
and
Simulation of MIMO Mobile Fading Channels
Prof. Dr.-Ing. HABIL. M. PÄTZOLD
Mobile Communications Group,
Faculty of Engineering and Science
Agder University College, Grooseveien 36,
NO-4876 Grimstad
Norway
Abstract:-For the development, analysis, and parameter optimization of cellular mobile systems, a profound knowledge of the mobile fading channel is indispensable. With regard to the development of future mobile communication systems employing multiple-input multiple-output (MIMO) techniques, there is currently a strong need for new channel models the statistical properties of which are sufficiently close to real-world channels.
In this plenary lecture, a general concept will be presented
for the development and simulation of realistic mobile fading channels models.
For illustrative purposes, a basic concept will first be introduced and
exemplarily applied to design classical Rayleigh and Rice fading channel models
often used to study the performance of single-input single-output systems. It
will then be shown how the basic concept can be extended to enable the modelling
of spatially correlated fading channels. The usefulness of the generalized
concept will be demonstrated by hand of elaborated space-time channels proposed
for MIMO mobile-to-mobile systems, where it is supposed that both the
transmitter and the receiver are moving. For such so-called MIMO
mobile-to-mobile channels, we will first introduce a proper geometrical model.
Starting from the geometrical model, it will be shown how a non-realizable
reference model and an efficient simulation model can be obtained. An overview
of commonly used parameter computation methods will be given and their
advantages and disadvantages will be discussed. For the important case of
isotropic scattering, a closed-form solution of the parameter computation
problem will be presented to enable the fitting of the statistical properties of
the developed MIMO channel simulator to those of the reference model with
arbitrarily precision. The lecture closes with some practice-relevant examples
of simulating MIMO mobile-to-mobile fading channels.
ROOM C
ROOM C’:
SESSION: Intelligent Agents and Applications
Chair: Dalibor Biolek, Mirka Miller, Antonio Zamora
|
Security & Trust in Agent-enabled E-commerce: Survey |
Haider Ali |
|
|
Developing Multi-Agent Systems: the Elektra meta-model and methodology |
Francesco Carbone, Ana Garcia-Serrano |
|
|
A Mobile Agent-based Architecture for Distributed Program Supervision Systems |
Naoufel Khayati, Wided Lejouad-Chaari - Sabine Moisan |
|
|
Implementation of ubiquitous digital systems and services |
Kyo-sun Song Gyeo-re Park Yu-raak Choi Sesangpyounghwa Lee Min-young Kim Yun-sam Kim Eun-sun Cho |
|
|
Modeling Communications of Mobile Software Agents Using Petri Nets |
Ali Pouyan, Steve Reeves, Ali Hassan Beigi |
|
|
Customized Design, Development, and Implementation of Distributed Control System for Process Control |
Qurban A. Memon, Habib-Ur Rehman |
|
|
MobileEVE : A Distributed System for Data Warehouse Maintenance under Schema Changes |
J. Akaichi |
|
|
Low-power aware design: Topics on low battery consumption |
Itziar Marin, Eduardo Arceredillo, Jagoba Arias, Aitzol Zuloaga, Iker Losada |
ROOM C’:
SPECIAL SESSION:
Grid Security
Chair - Organizer: Akshai Aggarwal Co-Chair: Matthias Pätzold, Janet Aisbett
|
Application of Importance Sampling in Simulation of Buffer Policies in ATM networks |
Samad S. Kolahi |
|
|
Arithmetic of Security Data Fusion under High Performance Computing Environment |
Xiao Haidong, Li Jianhua |
|
|
Analysis and Presentation of Distributed Sensor Data for Intrusion Detection |
John McEachen, Cheng Kah Wai, Vonda Olsavsky |
|
|
RFID Security and Privacy Concerns |
S. Srinivasan, Akshai Aggarwal, Anup Kumar |
|
|
Budgeting for Information Security and ROI Approach |
Akshai Aggarwal , Vishnu Kanhere, Shankar Kanhere , Nilesh Bajoria |
|
|
Study of a Discrete Iterative Map for Encryption Application in the Internet Part I |
Aggarwal A., Bakopoulos Y. , Soulioti V., Bardis N. , Kouremenos S. , Nikolopoulos S. |
ROOM C’:
SESSION: Wireless networks and telematics
Chair: Tom Coffey, K. Ioannou, Gorazd Kandus
|
Two Layer Call Admission Control Analysis in Microcellular Wireless Networks |
K.Ioannou, J.Pylarinos, S.Louvros, I.Panoutsopoulos, I.Kougias, S.Kotsopoulos,A.Garmpis |
|
|
Mean Waiting Time Analysis in Finite Storage Queues for Wireless Cellular Networks |
J.Pylarinos, S.Louvros, K.Ioannou, S.Kotsopoulos, A. Ioannou, A.Garmpis |
|
|
High Throughput Performance and Quality Issues of a Wimax System |
G.Agapiou, D.Vali, D.Charalambakis, P.Georgiadis, E.Plakidis, P.Rorris, K.Ioannou, A.Garmpis |
|
|
Vehicle Sensor Information Management Method |
YoungBag Moon, MinJeong Kim, YeonJun Choi, SunJung Kim, OhCheun Kwon |
|
|
A Wireless LAN-Based PDA Control Platform for Security Robots |
Hongwei Li, Changjiu Zhou |
|
|
Secure - Personal and Wireless Communications Systems |
Pedro Peris, Esther Palomar, Belen Ruiz, Arturo Ribagorda |
|
|
An Empirical Analysis of Automated Verification of Wireless Security Protocols |
Marian Ventuneac, Reiner Dojen, Tom Coffey |
|
|
A password-based mutual authentication protocol for wireless network |
Joongman Kim, DongMyung Shin, Yoojae Won, Byongjin Cho |
|
|
Optical Wireless Link for Railway Service |
Zdenek Kolka, Otakar Wilfert, Viera Biolkova, Dalibor Biolek |
|
|
Identification of devices in Bluetooth networks |
Zdenek Mikeska, Stanislav Hanus,Josef Vochyan |
|
|
Bluetooth and Wi-Fi Coexistence Simulation |
Jan Mikulka, Stanislav Hanus |
|
|
Terminal application middleware for the interoperability among telematics services |
Moon-Soo Lee, Jong-Woo Choi, Myung-Jin Lee, Kwon Oh-Cheon |
Saturday, December 17, 2005
ROOM C
ROOM C’:
SPECIAL SESSION:
Trust, Access, Privacy and Security
Chair-Organizer: Mirka Miller
|
Strategies For Matching Between Datasets Using Quasi-identifiers |
Janet Aisbett, Greg Gibbon |
|
|
Graphs connected with block ciphers |
Otokar Grosek, Pavol Zajac |
|
|
Graph representation of access controls for managing privacy, trust, and security requirements |
Geoff Skinner and Mirka Miller |
|
|
Matching Records on Birthdate, Sex And Locality |
Janet Aisbett, Greg Gibbon |
|
|
A Public Key Cryptosystem Based on Block Upper Triangular Matrices |
Rafael Alvarez Leandro Tortosa Jose-francisco Vicent Antonio Zamora |
|
|
Research on issuing a certificate and generating a private key of a home-gateway |
Baehyo Park, Jaeho Yoon, Seoklae Lee,Jonghyun Baek |
|
|
Privacy and e-Health in Australia |
Bruce Le Marshall, Mirka Miller |
|
|
Context-dependent Security Enforcement of Statistical Databases |
Vivek Mishra, Andrew Stranieri, Mirka Miller, Joe Ryan |
|
|
The Design and the Implementation of Web Service Security System for the Secured Distribution of Digital Contents |
Seungbae Yun, Hyunkjin Ko, Ungmo Kim |
|
|
Building up trust collaboration in p2p systems based on trusted computing platform |
Zheng Yan, Peng Zhang |
|
|
An Improved Attack on the Shrinking Generator |
P. Caballero-Gil and A. F·ster-Sabater |
ROOM C’:
SESSION: Cryptography and Secure Communication
Chair: Tom Coffey, Drago Zagar, John McEachen
|
A novel approach to secured and central logging data |
Nguyen anh Quynh,Yoshiyasu Takefuji |
|
|
A novel stealthy data capture tool for honeynet system |
Nguyen anh Quynh,Yoshiyasu Takefuji |
|
|
Secure Communication System over a GSM Network |
Rafael Alvarez, Jesus-Alberto Oliver, Jose-Francisco Vicent and Antonio Zamora |
|
|
A Viability Analysis of a Secure VoIP and Instant Messaging System on a Pocket PC Platform |
Jose-Vicente Aguirre, Rafael Alvarez, Jose Noguera, Leandro Tortosa and Antonio Zamora |
|
|
Parallelization of the AES Algorithm |
Wlodzimierz Bieleck,Dariusz Burak |
|
|
Modified Key Size Determination Models for Symmetric Ciphers |
Subariah Ibrahim and Mohd Aizaini Maarof |
|
|
Extending CAPSL for Logic-Based Verifications |
Liang Tian, Reiner Dojen, Tom Coffey |
|
|
Design of a Parallel Computing Based Cryptosystem |
Monica Dascalu,Eduard Franti,Lucian Milea,Teofil Teodorescu,Traian Balan,Angela Ionita |
ROOM C’:
SESSION: Information Security
Chair: Bruno Carpentieri, Orlando Belo, Zdenek Kolka
|
Strategic Alert Throttling for Intrusion Detection Systems |
Gianni Tedesco and Uwe Aickelin |
|
|
Computer Intrusion Detection with Clustering and Anomaly Detection, Using ICA and Rough Fuzzy |
Surat Srinoy, Werasuk Kurutach, Witcha Chimphlee, Siriporn Chimphlee,Santi Sounsri |
|
|
Dynamic monitoring model for bbs content security |
Jing Yu, Yanping Zhao |
|
|
Resolution based metamorphic computer virus detection using redundancy control strategy |
Ruo Ando Nguyen Anh Quynh Yoshiyasu Takefuji |
|
|
A Distributed Cooperative Multi-layer Security Architecture For Virtual Networks |
Simon O’Sullivan, Reiner Dojen, Tom Coffey |
|
|
Testing the Tools for IPv6 Traffic Tunneling |
Drago Zagar, Goran Martinovic and Snjezana Rimac-Drlje |
|
|
Study of Information Security Pre-Evaluation Model for New IT Service |
DongHoon Shin, SungHoon Kim, GangShin Lee, and Jea-Il Lee |
|
|
ITU-T X.805 based Vulnerability Analysis Method for Security Framework of End-to-End Network Services |
Young Duk Cho,Yoojae Won Byongjin Cho |
|
|
A Link-level Intrusion Detection Approach |
Hongjie Sun, Binxing Fang, Hongli Zhang |
|
|
A Bayesian Classification Model for Real-Time Computer Network Intrusion Detection Systems |
M. Mehdi, M. Bensebti, A. Anou and M. Djebari |
|
|
A study for vulnerability analysis and security reinforcement plan of accredited certification service |
Jonghyun Baek,Seoklae Lee,Jaeil Lee |
|
|
On formal verification methods for password-based protocols: CSP/FDR and AVISPA |
Abdelilah Tabet, SeongHan Shin, Kazukuni Kobara, Hideki Imai |
Sunday, December 18, 2005
ROOM C
ROOM C’:
SESSION: Algorithms and Applications
Chair: Ana Garcia-Serrano, Pedro Peris, Abdel Latif Abu Dalhoum
|
Hybrid Model for Computer Intrusion Detection |
Witcha Chimphlee, Mohd Noor Md Sap, Abdul Hanan Abdullah, Siriporn Chimphlee,Surat Srinoy |
|
|
Improving Zeng’s Technique for Color Re-indexing of Palette-Based Images |
Luca Matola and Bruno Carpentieri |
|
|
Recognition system for wooded species of Canary Laurisilva from its contour using kernel of Fisher |
Carlos M. Travieso, Juan C. Briceño, Jesús B. Alonso, Miguel A. Ferrer |
|
|
FPGA-based hardware implementation for network intrusion detection system rule matching module |
Mohamed Azab, Mohamed Rizk, Mohamed Abu-Elnasr |
|
|
Genetic and Swarm Algorithms for the Selection of OLAP Data Cubes |
Jorge Loureiro, Orlando Belo |
|
|
A Meta Knowledge Graph Modeling For View Definition Self Maintenance |
Jalel Akaichi |
|
|
Character recognition with histogram band analysis of encoded string and neural network |
Latesh Malik, SAndhya Arora, P.S. Deshpande |
|
|
Microprocessors fan speed control for dynamic thermal management |
Diary R. Suleiman, Hilmi F. Amin, Nuraddin Taha Husein |
|
|
TDS: The software for the early diagnosis of melanoma |
Ana González, Miguel A. Ferrer, Jesús B. Alonso, Carlos M. Travieso |
|
|
MLP/BP-based Decision Feedback Equalizers with High Skew Tolerance in Band-Limited Channels |
Terng-Ren Hsu, Jyh-Neng Yang, Terng-Yin Hsu, and Chen-Yi Lee |
|
|
Seeded search for joins in BCPOs |
Richard E. Moe |
ROOM C’:
SESSION: Internet, Data transmission and Protocols
Chair: A. Q. Ansari, Terng-Yin Hsu, K. Ioannou
|
Fuzzy shaper versus leaky bucket shaper in Voice over Internet |
F. D. Trujillo, A. J. Yuste, E. Casilari and A. Díaz–Estrella |
|
|
Migration towards Multimedia Next Generation Network |
L.Raptis, D.Kagklis, Y.Patikis, G.Hatzilias, N.Zervos, T.Zahariadis, D.Crhonis, K.Ioannou, A.Garmpis |
|
|
Reliability and Usability in Data Transmission Networks of the AMR System: A Pilot Study |
Petri Oksa, Mikael Soini, Jussi Nummela, Lauri Sydänheimo, Markku Kivikoski |
|
|
Measurement and Analysis of the Crosstalk Effect on the ADSL Data Transmission Rate |
Andjelko Kopecki, Josip Milanovic, Drago Zagar |
|
|
Single Fiber Lines in CESNET Backbone |
Karel Slavicek, Vaclav Novak |
|
|
Research of Heartbeat Detection Protocol Based on Multiple Master-nodes in Multi-machines Environment |
Dong Jian, Liu Hongwei, Yang Xiaozong |
|
|
Automatic Synthesis of Timed Protocol Specifications from Service Specifications |
Jehad Al Dallal |
|
|
On Convergence and Reliability in Self-Configuring Virtual Topologies |
Arso Savanovic |
ROOM A’:
SPECIAL SESSION: Artificial Intelligence and Soft Computing
Chair - Organizer: A. Q. Ansari
|
Adaptive device with underlying mechanism defined by a programming language |
Aparecido Valdemir de Freitas ,João José Neto |
|
|
Aggregating Subjective & Objective Measures ofWeb Search Quality using Modified Shimura Technique |
Rashid Ali, M. M. Sufyan Beg |
|
|
Automatic recognition of faces by neural networks and principal component analysis |
Ch. Bencheriet A.H. Boualleg H. Tebbikh |
|
|
A cognitive model based on representations that are spatial functions |
Janet Aisbett, Greg Gibbon |
|
|
Non-linear data for Neural Networks training and testing |
Abdel latif Abu dalhoum, Mohammed.Sadiq Al-rawi |
|
|
Knowledge Representation with Possibilistic-Certain Bayesian Networks |
Abdelkader Heni , Mohamed-Nazih Omri, Adel M Alimi |
ROOM C’:
SESSION: Communication Networks and Applications
Chair: K. Ioannou, Bruno Carpentieri, J. Al Dallal
|
The performance of multi-mode spatial MIMO system with imperfect CSI |
Gorazd Kandus, Sreco Plevel, Tomaz Javornik |
|
|
Impact of the Various Tiers of Interfering Cells on CDMA Systems |
Samad S. Kolahi |
|
|
Classes of sum-of-sinusoids Rayleigh fading channel simulators and their stationary and ergodic properties |
Matthias Pätzold, Bjørn Olaf Hogstad |
|
|
Evaluation of error rate performance of code spread CDMA system using simulations |
Ameya Naik, Meenal Tamhankar and Vikrant Joshi |
|
|
Towards a Better Understanding of Efficiency in mGovernment Services |
Tarek El-kiki, Elaine Lawrence |
|
|
Parameterized Soft IP Core of High Performance ARINC 429 and UART Interfaces |
Usman Yousaf, Muhammad Asif, Imran Qadeer |
|
|
Protection Switching Scheme for NG-SDH based Switching System |
Kiwon Kim, Byungho Yae |
|
|
Interference analysis in 2.5G network |
Filip Gleissner,Stanislav Hanus |
|
|
Crosstalk and Isolation measurements in copper wires |
G.Agapiou, T.Doukoglou, P.Georgiadis, G.Georgakopoulos, E.Plakidis, P.Rorris, K.Ioannou, A.Ioannou, A.Garmpis |
|
|
A Practical Implementation of a Wavelet Based Filtered Multitone Modulation |
Roman m. Vitenberg |
|
|
More Privacy in Context-aware Platforms: User Controlled Access Right Delegation using Kerberos |
Peter Langendoerfer, Krzysztof Piotrowski |
|
|
A lightweight and scalable VoIP platform based on MGCP/H.323 interworking and QoS management capabilities |
T. Dagiuklas, K.Ioannou, A.Garmpis |
ROOM C’:
SESSION: Advances on Information Science & Communications
Chair: K. Ioannou
|
Dynamical Systems and Step-2 Nilpotent sub-Riemannian Geometry |
A. Anzaldo-Meneses, F. Monroy-Perez |
|
| Shape analysis of left ventricle using spherical harmonics functions | A. Ben Abdallah, H. Essabbah, M. H. Bedoui | 508-371 |
| Complex analysis of outputs from driving simulator experiments focused on drowsiness detection | Petr Bouchner, Michal Hajny, Stanislav Novotny, Roman Pieknik | 508-297 |